2016 Verizon Breach Investigations Report (Part 1 of 3)
The 80 page report is packed with valuable data breach insights. We know time is valuable so we decided to save you some by sharing the 3 main topics you should understand from this report.
How many days go by between news stories involving computer breaches? The truth of the matter is that as long as sensitive data is gathered by merchants, thieves will attempt to steal it.
The number of data breaches continues to increase. Cybercrime affects your brand, your customers and your employees in ways that are unrecoverable at times. Don't let your business be affected next.
Persistent threats affecting businesses of all sizes and in all verticals are becoming more consistent and hitting more frequently. The 2016 Verizon Data Breach report analyzed 100,000 incidents, of which 3,141 were confirmed data breaches.
It's National Small Business Week! Let's celebrate the hard work you do and make sure your business continues to grow. Have you ever thought about what would happen if your business is affected by a data breach?
2016 Verizon Breach Investigations Report (Part 2 of 3)
In our previous post we showed you that regardless of the business’ size, location or industry, many are targets to hackers. So how are hackers getting into these businesses’ networks and stealing data?
Though there are many companies out there responsible for securing merchant locations from the risks of data breaches, people’s own risky behavior often leads to their ID theft problems, no matter how well merchants protect them. And with more and more merchants accepting chip cards this year, hackers are likely to go back to tried and true methods for preying on individual cardholders.
In the wake of BackOff, and numerous other data breaches, consumers are demanding answers into the how and why surrounding companies who have inadvertently allowed data to be compromised given security measures accessible today.
Passwords keep your accounts and network safe but may also be a gateway for hackers. Here are some quick tips we recommend when creating your passwords.
With data breaches and Snowden-like information grabs, I’m getting increased requests for how to track data moving to and from removable storage, such as flash drives. The good news is that the Windows Security Log does offer a way to audit removable storage access.
Following many high-profile data breaches, consumers have elevated data privacy to front-page news and included it as criteria for brand selection and engagement. Consumers around the globe now realize that they aren’t always aware or informed about how their private information is used or shared. Fifty-four percent of consumers are more concerned with protecting their personal information than they were a year ago, according to a survey reported by Security Magazine.
With distressing regularity, new breaches continue to make headlines. The biggest companies, the largest institutions both private and government are affected. Every sector is in the news.
Threat Summary: On September 11th, 2023, MGM Resorts suffered a crippling ransomware attack that resulted in 10 days of computer system downtime as well as an estimated overall loss of $80,000,000. The threat actor, dubbed Scattered Spider, is claiming ownership of this hack and alleges to have ties with the infamous ALPHV/BlackCat ransomware gang. In […]
In this fifth article of the series, we continue to explore the basic ways businesses can keep their networks safer. These include tools you can implement on your own and understand why taking action is vital to the safety of your business.
Business uncertainty has led to widespread adoption of working from home. Since most meaningful tasks in any organization require teamwork, this remote work approach has naturally led to a dramatic rise in the use of collaboration tools such as Zoom Conferencing.
Nearly 60% of businesses have experienced a breach in the last two years. Have you ever considered what would happen if your business was breached? Do you have a plan of action?
Threat Summary: Storm-0558 is suspected to be a China-based, nation-state threat actor whose TTPs are closely aligned with espionage objectives. This threat actor managed to compromise an inactive MSA signing key which was then used to sign fabricated authentication tokens. Authentication tokens are short-lived credentials that are used to authenticate users to a service. They […]
Discover how Lumifi's expertise strengthened cybersecurity for state and local government agencies. By deploying a centralized security technology stack, agencies experienced increased response capabilities and reduced visibility gaps. The experienced SOC provided invaluable support, ensuring optimal protection against diverse attack types. Explore the case study for the full success story.
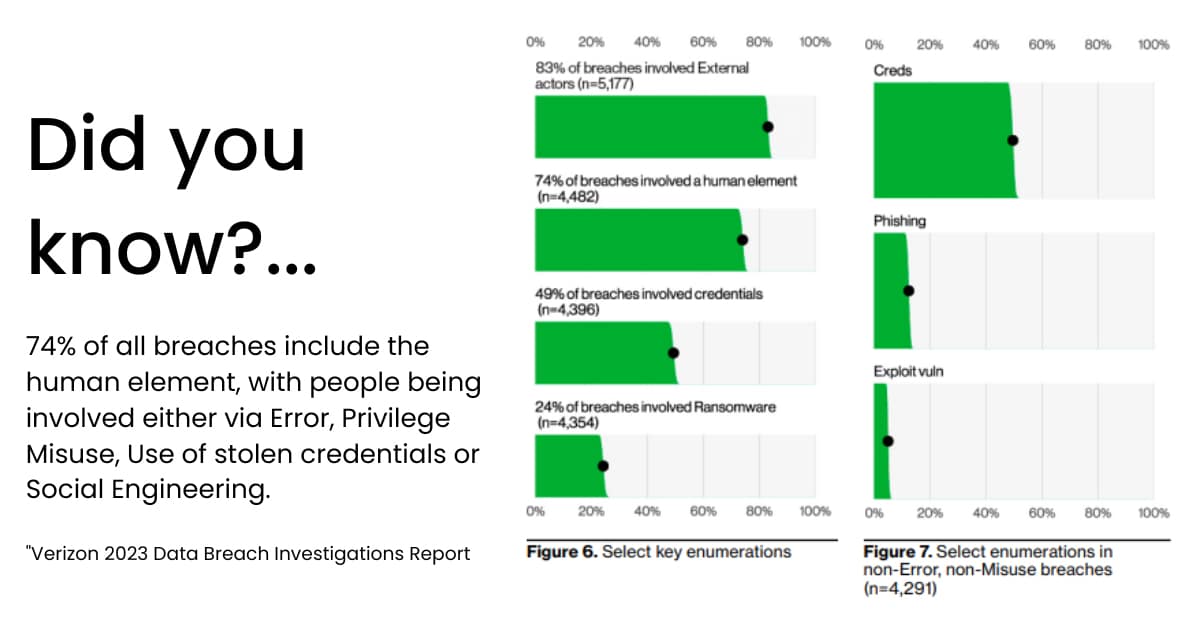
Cybercriminals are adopting new, more sophisticated tactics. Security leaders can't depend on purely technical solutions that ignore the human element. If there is one broad theme to Verizon's 2023 Data Breach Report, it's that the arms race between cybercriminals and cybersecurity professionals hinges on the human element more than ever. The report declares this clearly […]
The use of stolen or compromised credentials remains the most common cause of a data breach. It was responsible for 19% of breaches studied by IBM in 2022. The reason? These attacks are relatively easy to plan and execute.
There’s an old saying: Their bark is worse than their bite. However, this is not the case with the penalties of non-compliance when it comes to the General Data Protection Regulation (GDPR). With the enforcement date of the GDPR having passed on May 25, 2018, any company not in compliance could be in for a very nasty shock.
How do you figure out when someone was actually logged onto their PC? The data is there in the security log, but it’s so much harder than you’d think.
What is the true cost of a data breach? A data breach affects your business, brand, and reputation. But it can be prevented.
It is becoming more and more frequent to read about electronic data breaches in the news these days. Unfortunately, what is not touched on as frequently are the physical security issues present in restaurant and retail establishments.
Many of our customers and resellers have asked how Heartbleed affected Netsurion services. In a nutshell, the managed services that make up our product offerings were not directly affected by Heartbleed.
The old Haunted Hotel with squeaky wood floors, welcomed all guests who dared enter the front doors. Guests arrived from every nation – every corner of world – ready to spend money and explore.
As I reflect on this year, a Shakespearean quote plays out in my mind – when King Henry the Fifth is rallying his troops to attack a breach, or gap, in the wall of a city, “Once more unto the breach, dear friends”...
As data breaches occur more and more, it is no secret that the market needs more cybersecurity professionals. Here are a few statistics on the need to educate the next generation on pursuing cyber professional careers.
When business owners start looking at Point-of-Sale (POS) systems, they may feel overwhelmed at the infinite amount of options they can find online. How does a business owner make a decision? How do they know it’s the right decision?
Equifax, one of the big-three US credit bureaus, disclosed a major data breach. It affects 143 million individuals — mostly Americans, although data belonging to citizens of other countries, for the most part Canada and the United Kingdom, were also hit.
The gap between the ‘time to compromise’ and the ‘time to discover’ is the detection deficit. According to Verizon DBIR, the trend lines of these have been diverging significantly in the past few years. Worse yet, the data shows that attackers are able to compromise the victim in days but thereafter are able to spend an average of 243 days undetected within the enterprise network before they are exposed.
Cyberattacks against banks and financial institutions continue to rise as cybercriminals develop new tactics. The global financial sector is one of the biggest cybercrime targets in the world. The volume and sophistication of cyberattacks on banks surged in 2022, spiking considerably at the very end of the year.
A data breach has serious consequences both directly and indirectly. Lost revenue and a tarnished brand reputation both inflict harm long after incident resolution and post breach clean-up. Still, many organizations don’t take necessary steps to protect themselves from a potentially detrimental breach.
Every online action you perform involves sharing a bit of data – over time, that data can add up. Successful organizations and influential people rely on the public Internet to promote their brands, ideas, and products. A significant amount of time and energy goes into building a brand, and most of it is spent online.