One of the most protective mechanisms at the heart the Security Operations Centers (SOC) is a dedicated hub that monitors, detects, and responds to cyber threats in real-time. The SOC acts as the nervous system for cybersecurity operations, tirelessly working to ensure potential vulnerabilities are identified and neutralized before they can escalate.
As cyber threats evolve, the traditional SOC model has had to adapt to keep pace. Enter the concept of the SOC Visibility Triad, a strategic framework that redefines and enhances the way security operations are conducted. First introduced in the Gartner research report, "Apply Network-Centric Approaches for Threat Detection and Response"1. This holistic, three-pronged SOC approach empowers organizations to gain clearer visibility into threats and to respond more effectively.
As we dive into this transformative concept, senior technical managers and executive decision-makers will understand its crucial role in fortifying an organization's cyber defenses and why considering MDR service providers who embrace this methodology can be a game-changer.
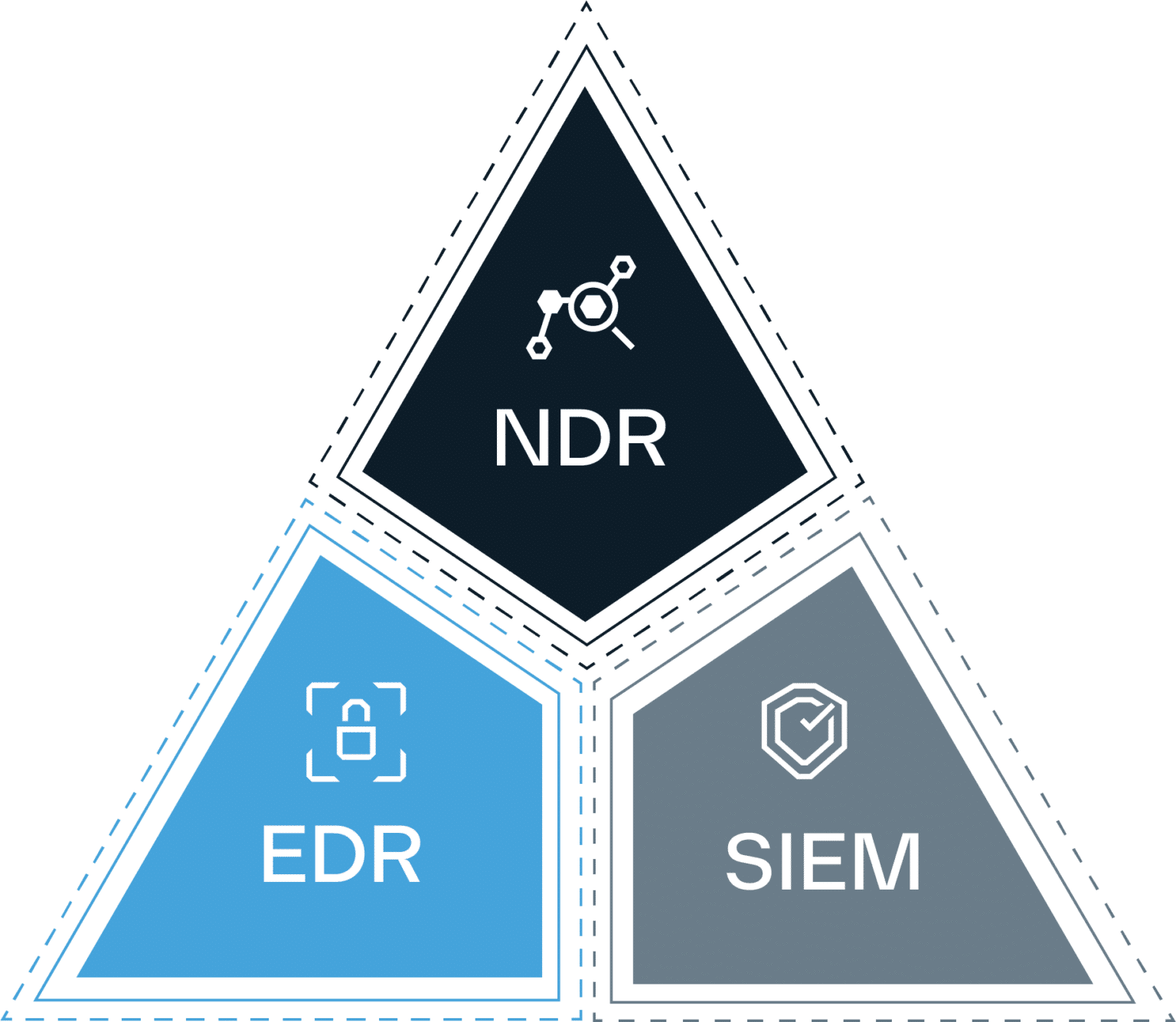
The SOC Visibility Triad is a framework for equipping security teams with the capabilities they need to effectively detect, investigate, respond, and remediate threats. It consists of three core technologies that give analysts in-depth knowledge of their security posture and complete visibility into security events:
Gain real-time insight into endpoint threats and block malicious activity before it leads to business disruption. Secure your organization’s laptops, desktops, and mobile devices with best-in-class solutions configured to counter the latest threats.
Catch attackers after they gain entry to your network. Analyze network traffic to prevent lateral movement and leverage behavioral data to gain security insights. Eliminate blind spots in your network and catch malicious insiders before they have a chance to attack.
Collect and analyze log data from every corner of your organization. Pinpoint security events and launch detailed investigations in response. Gather and correlate data from across your entire IT infrastructure to find and analyze threats with customized detection rules.
Lumifi’s proprietary SOC automation service gives security teams detailed information on security events and alerts in near real-time. ShieldVision™ alerts draw from each pillar of the SOC Visibility Triad, providing our customers with complete visibility and actionable intelligence on security issues as they occur.
Our proactive, context-aware approach unifies insights from across the entire tech stack, giving analysts the data they need to make confident security decisions when it matters most.

Lumifi's Managed Detection and Response services leverage all three components of the SOC Visibility Triad to provide flexible, integrated security services to companies of all sizes — without locking them into relationships with specific vendors in the process.
We strongly believe that Knowledge is Your Best Defense, and that opaque, uncommunicative systems get in the way of operational security excellence. Our team customizes SIEM, EDR, and NDR deployments to remove these obstacles and achieve Glass Box functionality — granting full visibility and transparency to security operations so our customers can manage risk and optimize security outcomes across the entire tech stack.