Digital technology is critical to most businesses today. But as automation and connectivity grow more integrated into daily operations, they increase the risk of cyberattacks and exposure to threats. The best way to prepare and protect your company is through working with a Managed Detection and Response partner that is actively threat hunting on your organization' behalf.
Threat hunting is a proactive defense activity that entails a comprehensive search of networks, endpoints, and datasets for threats that have previously evaded detection by technologies. These threats are often malicious, suspicious, and risky, as well as concealed. However, using threat intelligence, threat hunting uncovers them before an attack can happen.
Threat intelligence collects and analyzes data about successful and attempted intrusions using machine learning and artificial intelligence. The information acquired enables enterprises to make informed decisions on defending themselves against security threats and attacks on their assets.
Utilizing threat intelligence, cyber threat detection professionals are better equipped to manage threats and can respond faster to alerts of potentially harmful interactions. Threat intelligence offers significant benefits, including prevention of data breaches, protection of sensitive information, detection and response to advanced threats, and reduced cybercrime incidents and fraud-related costs.
Effective threat hunting relies heavily on cyber threat intelligence, so it' crucial that your organization can easily share comprehensive and cohesive data among security operations, incident response, and threat intelligence teams, as well as to your peers.
However, doing so is not simple—hurdles like cross-team collaboration, security data silos, data discovery, and restricted access prevent the implementation of a unified cyber defense strategy across organizations. And it makes your company more vulnerable.
Anomali has created threat intelligence-driven solutions to improve security defenses through extended detection and response capabilities, allowing organizations to prevent attacks from happening.
When it comes to threat hunting tools, Anomali offers three products: ThreatStream, Match, and Lens.
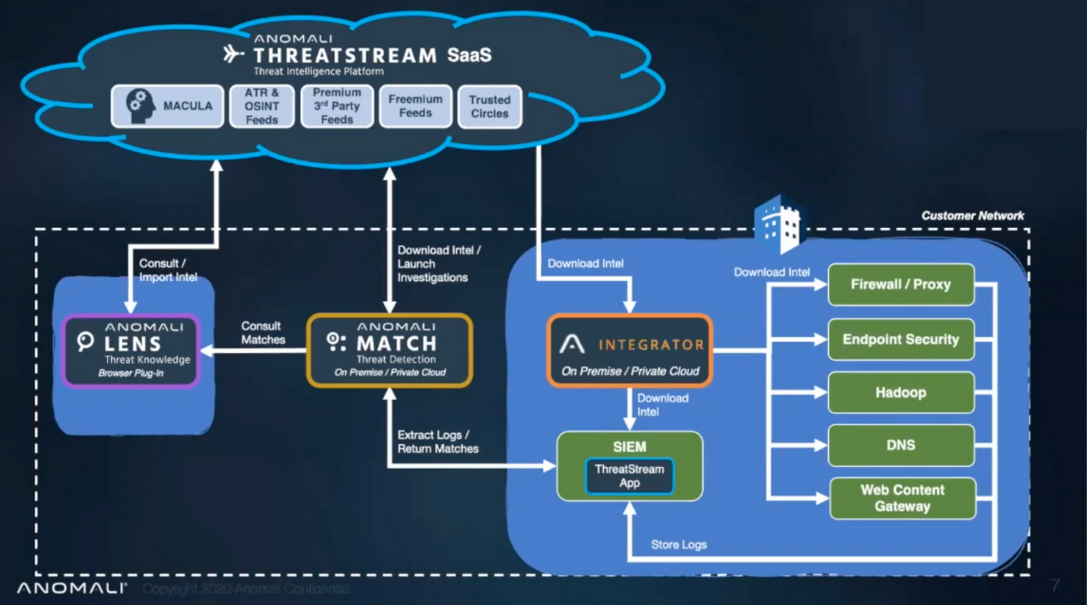
Above you will find a diagram of how Castra utilizes Anomali Threatstream and Lens tools for our clients.
Lumifi leverages ThreatStream to automate threat intelligence collection from a variety of sources, including curated Anomali Labs feeds, open-source OSINT feeds, specialized premium feeds, and information sharing and analysis centers (ISACs). It processes the data set thoroughly to minimize false positives, allowing your team to distinguish between what to be wary of and what to ignore.
ThreatStream disseminates curated information to your organization' security systems, including SIEM, firewall or proxy, endpoint security, and SOAR, for monitoring and blocking.
As Anomali' XDR solution, Match pulls data from ThreatStream and your organization' history to identify a threat and the severity of its impact on you. It can pinpoint relevant threats and give security teams actionable intelligence to make informed decisions, especially for historical and newly identified threats.
The Lens is an internet browser extension that hunts threats by automatically scanning web-based content and PDFs for hidden threat data, such as threat indicators, threat actors, malware, or attack tactics. It lets analysts import scanned threat data to ThreatStream or Match and use them for reporting or collaborating.
For effective threat hunting, Castra uses ThreatStream and Lens.
Ensure your company' assets are highly secure all the time with cyber threat hunting. Partner with Castra, and let us identify indicators of compromise, and fine-tune your SIEM technology with industry-specific data, so you can focus on what matters the most.
