
Malicious insider attacks are a complex challenge for cybersecurity professionals. Because these attacks rarely involve malware, it is essential that security teams have technology in place that can help detect malicious behaviors, not just malicious content. This is necessary to help identify insiders who may be a threat.
Insider threats are usually associated with employees or contractors within an organization who have malicious intent or are simply careless in their online behaviors. Likewise, bad actors that enter the network through a compromised credential attack might also be considered a malicious insider after the fact.

Bad actors intentionally abuse their privileged access to steal information or degrade systems for financial, personal, and/or malicious reasons. These malicious users are often assumed to be valued employees performing daily tasks based on their roles and access levels.
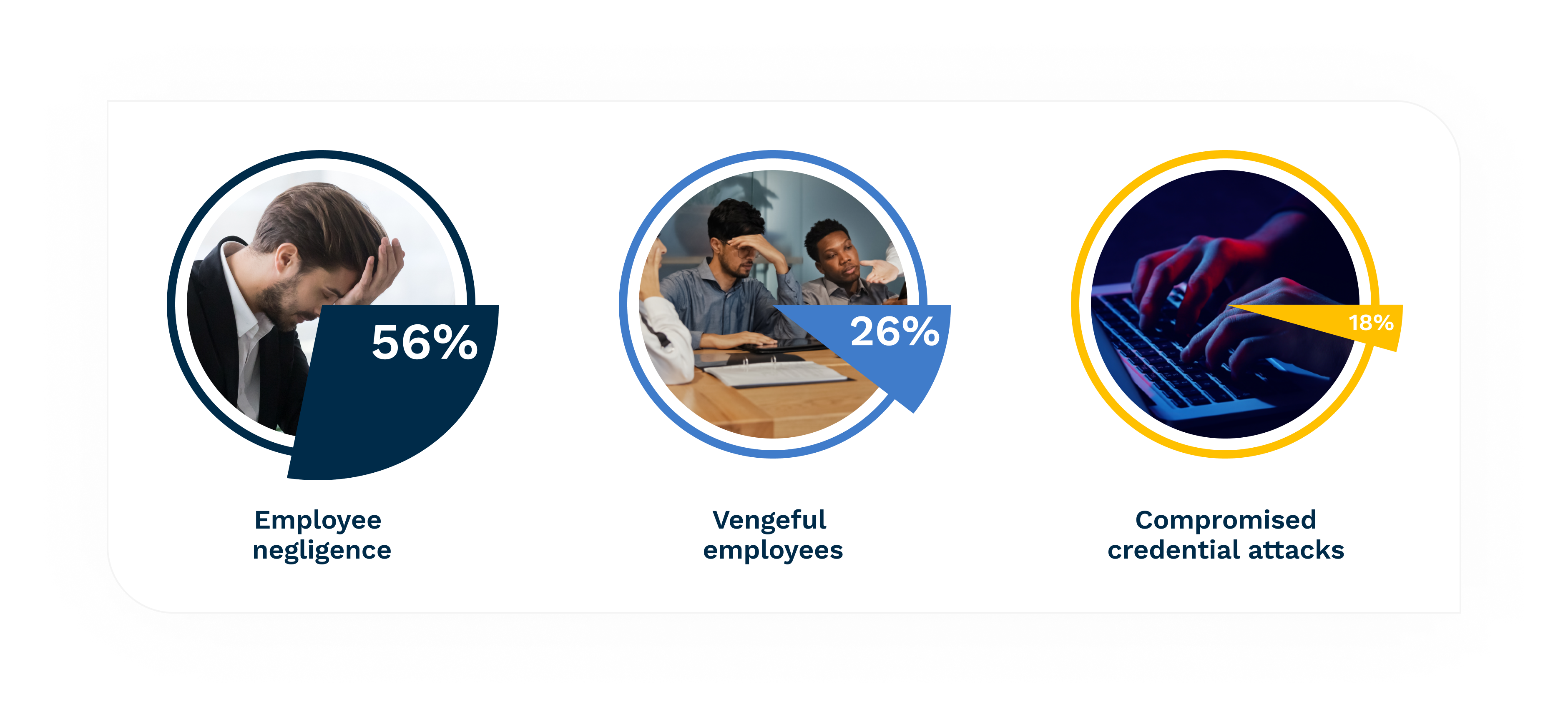
Source: 2022 Cost of Insider Threats Global Report (Ponemon Institute)[1]
Collectively, these three attack types cost financial services organizations $21.25 million annually, according to the same report.
The impact of negligent employees is significant, and usually the result of their apathy and poor security practices that either cause immediate harm or create opportunities to be exploited by an outside source.

More than half of the attacks studied were caused by employee or contractor negligence. It cost on average $484,931 per incident.[2] Many times these incidents occurred due to improper employee training and awareness. Likely, the employee did not ensure their devices were secured, did not follow company security policy, or forgot to patch and upgrade.

Bad actors and vengeful employees are intentional in their actions and try to stay "under the radar" to execute a specific plan of attack without generating any suspicion. In any case, these malicious users are assumed to be valued employees performing daily tasks based on their roles and access levels. And since there is usually no malicious content that can be detected, security teams must focus on detecting behavioral anomalies.
A former JP Morgan Chase Bank employee was sentenced to four years in prison for selling customer account information. He would also use that information himself to make unauthorized withdrawals from customer accounts. The employee' scheme was uncovered when he sold this information to a confidential informant and to an undercover law enforcement officer. The United States Attorney said the employee abused his position by victimizing unsuspecting customers.
A Canadian financial services firm, Desjardins, suffered a massive data breach in 2019, caused by an employee who stole the personal information of more than 4 million users. Desjardins said the employee leaked that information, which included social insurance numbers, addresses, and banking habit details. Desjardins reached a $157 million settlement with plaintiffs.
A trader at a major financial services organization and a retired financial professional were charged in December 2022 with running an extensive insider trading scheme based on stolen confidential trade information from that organization. The government said they made tens of millions of dollars in profits. The U.S. attorney said the trader betrayed the trust and confidence of his employer.
In a SOC where security teams rely on a legacy SIEM, this kind of attack can be virtually undetectable. These systems don't easily analyze user behaviors, so compromised accounts and malicious insiders trigger very few results. Cybercriminal groups know this. That' why some have begun actively recruiting corporate insiders and sharing illicit profits with them. Financial institutions are a compelling target because they typically have robust perimeter defenses that take time and effort to overcome. The financial services industry is also attractive to bad actors because it' worth $20.49 trillion worldwide and makes up approximately 20-25% of the global economy.
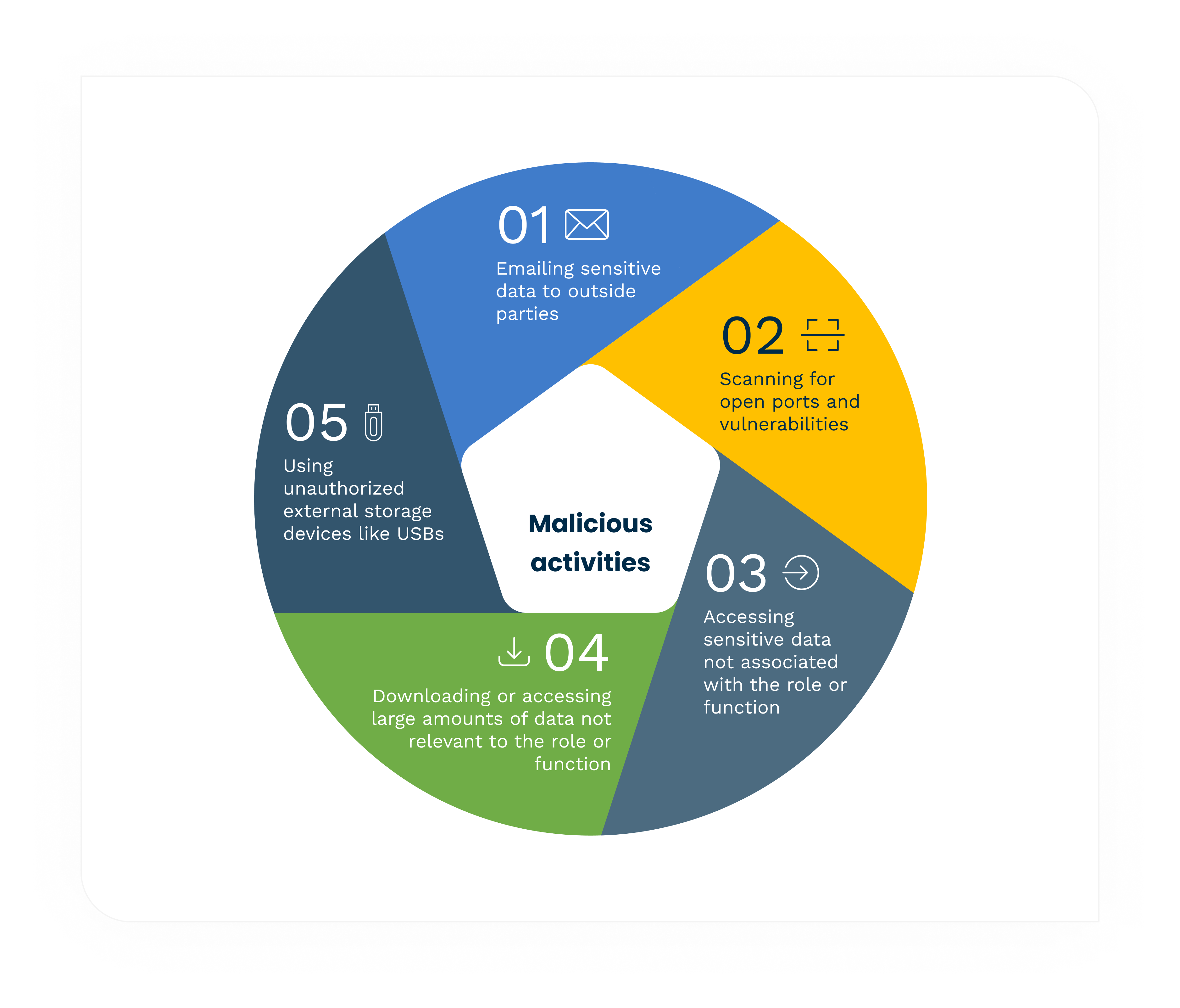
When the Ponemon Institute studied insider threats, 74% of respondents said malicious insiders relied primarily on corporate email to steal sensitive data. These are the top five tactics they used.
Insider threats are one of the most challenging security threats in the financial sector. Once attackers compromise a privileged account, they can move laterally through the organization, escalate their privileges, and exfiltrate data.

In an analysis of more than 6,800 insider incidents, malicious insiders caused 26% of incidents at an average cost of $648,062 each. The largest costs are the impact of business disruption (23% of total cost) and technology (21% of total cost).[3]
The annual cost of overall insider-related incidents varies based on the size of the organization. Financial services have the highest average activity costs at $21.25 million, followed by services (such as law, consulting, and accounting firms) at $18.65 million.
Insider attacks are not just costly, they are time-consuming for an organization' security team. One insider security incident can take about 85 days to contain. Companies spend the most money on containment, followed by investigative costs.

The Ponemon Institute released the 2022 Cost of Insider Threats Global Report, outlining five signs an organization is at risk for a malicious insider attack:

User and entity behavior analytics (UEBA) has become an essential technology to help reduce the risk and impact of insider threats. Next-generation SIEMs, such as those from Exabeam, integrate this essential UEBA intelligence within their platforms. Whenever a user, device, or database starts to behave in a way that breaks its established norm, it is assigned a certain score. When that score accumulates beyond a certain threshold, an alarm is triggered and an investigation begins. With a properly tuned SIEM, security teams can often gain insights into suspicious user behaviors before the bad actor or vengeful employee can achieve its objectives.
Traditional cybersecurity approaches are not effective against malicious insiders for two main reasons:
Customers place a great degree of trust in financial institutions. Protecting customer accounts from malicious insiders is an implicit condition of that trust. Advanced SIEM capabilities and XDR-powered threat mitigation can help finance organizations earn that trust.

Lumifi can help you deploy UEBA technology and protect your financial institution from malicious insiders. As an expert-managed detection and response partner, we specialize in using best-in-class SIEM technologies like Exabeam and USM Anywhere to catch and prevent malicious insiders in complex enterprise environments.
Schedule a demo to find out how Lumifi can enhance your security posture and detect an insider attack before it happens.
[1]https://protectera.com.au/wp-content/uploads/2022/03/The-Cost-of-Insider-Threats-2022-Global-Report.pdf
