Lumifi can now combine the power of Netshield's active blocking with AlienVault's USM and immediately block rogue devices AND monitor egress network traffic to effectively block malicious behaviors like malware and phishing.
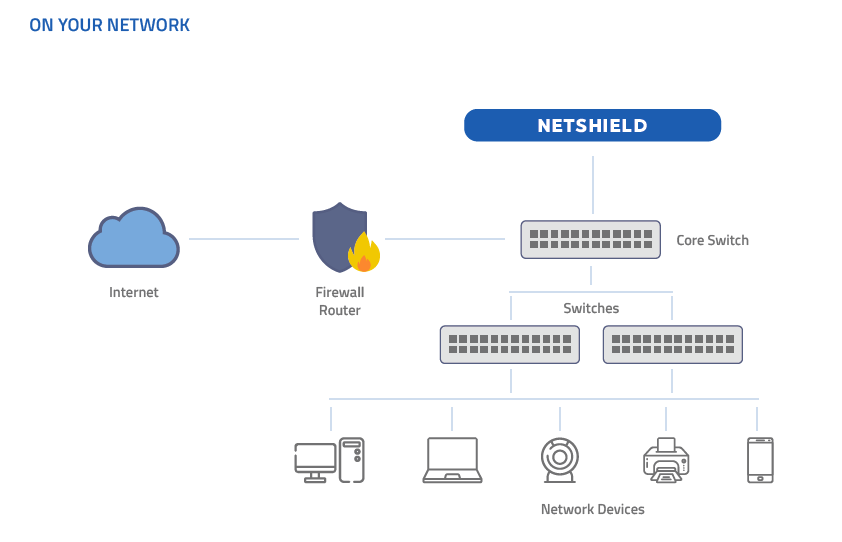
Through the power of Netshield's Network Access Control (NAC), Lumifi can offer unrivaled protection for the inside of your network. Firewalls are a necessity for protecting networks against outside threats. However, today' biggest threats come from the inside of the network. By leveraging Netshield, Lumifi can secure your network while enabling the adaptability and flexibility required to support workforce mobility and business continuity.
It starts with visibility. An explosion in the number of devices attempting to connect to every network, including smart IoT devices and mobile and other BYOD, demands effective asset detection to know what is on the network so devices cannot hide. But visibility is only the first step.
Once seen, threats must be blocked. Devices that don't belong must be quarantined. When human behavior inside the network launches malware, phishing, and other types of threats, those devices must also be blocked to protect your data and your business. Go beyond monitoring and reporting with intelligent, automated, instant threat blocking.
Finally, stay ahead of threats with network auditing for common threats and vulnerabilities. By utilizing Netshield, Lumifi can conduct a comprehensive, detailed scan of every device on your network allowing us to stay ahead of threats and prepare for external audits and other reporting.
Gartner – Why do companies need Network Access Control?
Response to Audit Findings - "Many organizations pass through third-party security assessments...the most common finding is the ability to connect to internal infrastructure with no identification of the device...which increases the risk of internal attacks by unauthorized devices."
Improve Network Visibility - "Network Access Control can...reduce the risks associated with noncompliant devices."
Incident Response - "When an alert occurs, an automated mechanism will remove the endpoint." IoT Proliferation "IoT devices...used in large-scale...series of distributed denial of service (DDoS) botnet attacks"
Why Does Lumifi Prefer Netshield?
Most NAC solutions are designed for the needs and budgets of a large enterprise. Netshield is different. Like Lumifi, they believe that a limited budget and limited staff should not require a compromise in having comprehensive network security. Our services deliver a powerful mix of functionality and value. Optimal network security requires layers of interlocking protection, and Netshield provides many critical security elements in an affordable and manageable solution.
Network Visibility
Instant ID: Operating at Layer 2, Netshield instantly identifies every device that is connected or attempting to connect to your network, including physical, virtual, mobile, and IoT. Netshield creates a comprehensive inventory, profiling and classifying each device on a network - devices cannot hide from Netshield.
Agentless: Netshield sees every device without the need for an agent. Agent-based solutions can take months and hundreds of hours of staff time, and agents cannot even be loaded on most IoT or private devices. Virtually every new Netshield deployment identifies assets that were not listed on the original asset inventory. The first step in trusting your network is knowing what is on your network.
How: Netshield' Asset Detection Engine looks at ARPs and ARP requests along with DHCP requests and IP traffic to identify devices on the network whether wired, wireless, IoT, BYOD, or Virtual.
Network Access
Rogue Devices Denied: You determine which devices are to gain network access. Those devices not trusted - whether known or newly entering the network – are blocked until access is granted.
New Devices Seen Immediately: With billions of IoT and BYOD devices, along with guests, contractors, and more, rest assured none will enter your network unnoticed, and none will have access unless you trust them, including devices spoofing a MAC address.
How: The Blocking Engine prevents untrusted/known-bad devices from participating on the network by sending a small stream of traffic to block a device while all other devices on the network segment are prevented from seeing the blocked device.
Threat Blocking
Zero-Day Malware & Phishing: Devices attempting to connect to outside command and control servers that are identified as bad actors trigger an alert and are instantly blocked – a Machine Time response to stop Machine Time threats to your network.
Anomalous Behavior via Integration: Netshield seamlessly integrates with multiple log analysis, SIEM, and A/I driven threat detection tools to block the behaviors they flag as dangerous, based upon your rules for balancing security and business continuity.
TLD and Site-Specific Blocking: Netshield also allows for identification of high-risk destinations and blocks access accordingly.
How: The Malware Detection Engine monitors egress traffic looking for connection attempts to known Malware and Phishing sites. When such traffic is detected, the Blocking Engine is then triggered to instantly isolate the offending device and using switch integration can shut off the port or move the device to a quarantine VLAN. Multiple public and private lists of known bad sites are combined and uploaded every three hours to provide zero-day protection.
Vulnerability Auditing
Common Vulnerabilities and Exposures (CVE) Scanning: Netshield interrogates every device on the network and produces a detailed report of vulnerabilities and exposures. This report includes comprehensive reporting for every scan by device along with investigative and educational tools for background on the specific CVEs and remedies.
How: The on-board Auditing Engine executes thousands of scripts to identify Common Vulnerabilities and Exposures (CVE) by probing devices for open ports, default logins and settings, vulnerable applications and more. Over 8 thousand scripts are employed with new scripts regularly added as new vulnerabilities are discovered.
Additional Features