On-demand Exabeam Expertise Unlocks SIEM Value for AECOM
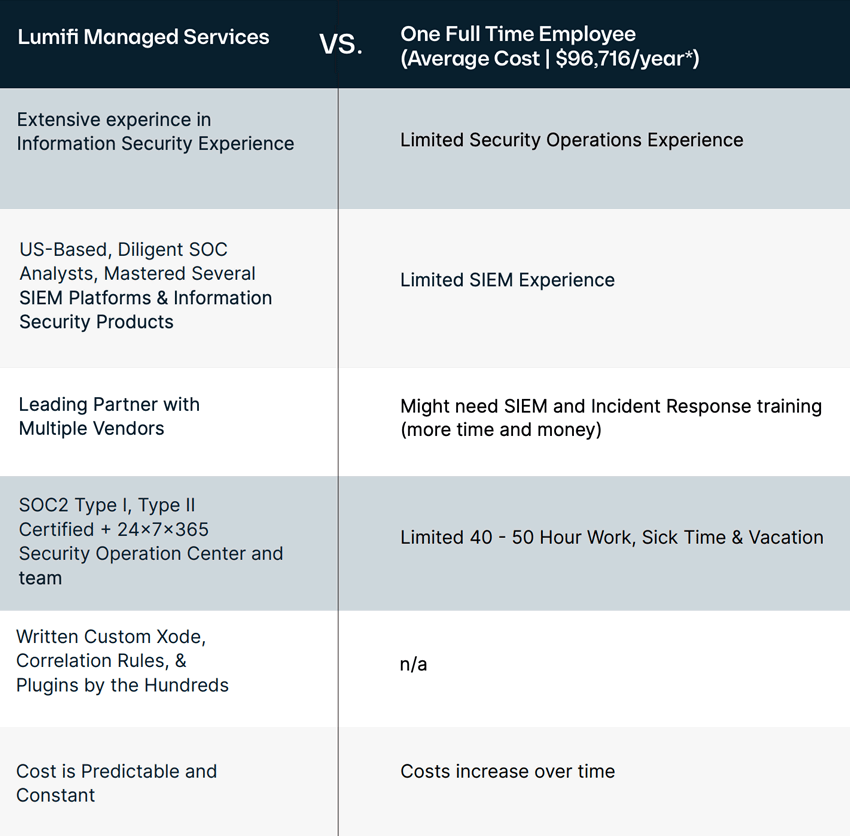
Lumifi helps organizations solve complex SIEM deployment problems and maximize the value
Our Customer: AECOM is a publicly traded critical infrastructure consultancy and Fortune 200 member with 50,000 employees located around the globe. As one of the largest companies in the United States, AECOM plays a major role in building skyscrapers, mass transit terminals, concert halls, and everything in between.
The company has worked hard to achieve recognition as the World’s #1 Most Admired Company, securing Fortune magazine’s top spot for three consecutive years. With a pipeline full of multi-billion-dollar projects of government customers, AECOM can’t afford any less than the highest standards of credibility and security.
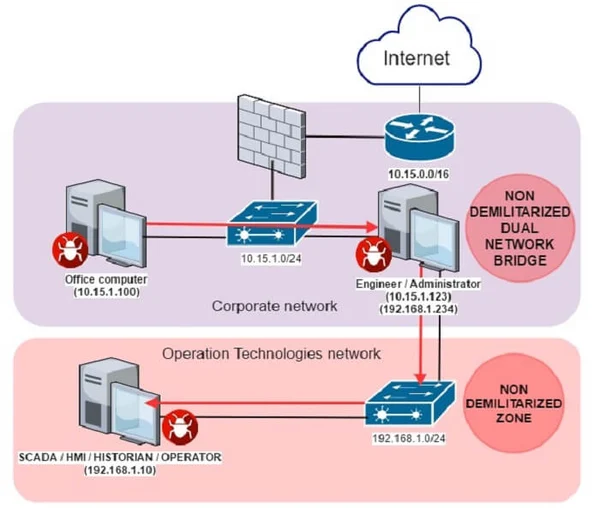
By the time AECOM reached out to Lumifi, it had spent two years working with a provider to successfully deploy its Exabeam SIEM. The organization was stuck in the development phase and could not get the SIEM platform to ingest all of AECOM’s global data sources correctly. AECOM couldn’t achieve holistic visibility into its security posture, leaving its organization exposed to sophisticated attacks while its security team poured resources into a never-ending development process.
AECOM’S Security Challenges: As a market-leading infrastructure consultancy managing some of the world’s largest projects, AECOM regularly faces incredibly sophisticated attacks from a wide range of sources. Managing these projects responsibly requires deep visibility into security risks, machine learning-enabled automation, and User Entity and Behavioral Analytics (UEBA) technology. The Exabeam platform provides all of these capabilities. However, the process of completing such a large implementation is complex. AECOM’s previous security provider did not have the product expertise necessary to ensure streamlined deployment.
AECOM needed SIEM expertise to leverage Exabeam to deliver on several core needs:
- UEBA-Enhanced Insight
- Log Management & Analysis
- 24×7 Security Operations
- Custom Rules & Dashboards
- Orchestrated, Automated Threat
- Response Playbooks
Successful SIEM Implementation with Unlimited Visibility and Customization Lumifi was instrumental in turning AECOM’s stalled SIEM deployment around, enabling the company to gain a unified, central view of all security events – including both internal and external threats, cloud activity, and on-premises vulnerabilities. After spending two years stuck in the deployment phase, AECOM was able to finally leverage the full power of Exabeam. In two months, Lumifi has accomplished more than the previous two years of trial-and-error with a less capable vendor. Lumifi’s product expertise helped AECOM deploy a detailed model of normal user and asset behavior in Exabeam. This model provides constant, real-time information on the risks of insider threats and credential-based attacks. Lumifi became an extension of AECOM’s Security Operations Center, providing Exabeam expertise on-demand, 24×7 detection and response, and custom rules, models, reports, and dashboards.
The Results:
- True 24×7 visibility and behavioral modeling for every user and asset in the organization’s IT infrastructure.
- Successful integration of AECOM’s existing security tools into a consolidated Security Orchestration, Automation, and Response (SOAR) platform.
- Ongoing customization to refine AECOM’s detection and response capabilities and adapt to a constantly changing threat landscape.
Technology Description:
Thank you for the service that Lumifi has provided over the last year to AECOM! Lumifi provided the services AECOM needed to keep the organization safe. You have helped us bridge a gap that continued to widen on us, and we appreciate the talent and work that Lumifi put into it. Lumifi has the grit and passion necessary to provide valuable MDR services in some of the toughest environments. I would absolutely recommend working with Lumifi they bring a lot of value to the table.
- - Paul Dial, CISO, AECOM projects.